The Cryptolocker virus out there in the wild and I’ve seen it happen on a few computers and it’s certainly not pretty. The details are sorrid, but in a nutshell what happens is a crytolocker virus gets onto your computer, locks all your pertinent files and demands a ransom amount so you can get your files back. Those who pay the ones delivering the virus will become more bold and will start demanding more money.
What can you do to protect your company?
Create some Group Policies to lock down likely places for Malware / Spyware / Grayware / Cryptodefense and other likely .exe programs from running:
– Open up Group Policy and create new GPO
– Title this policy Disable .exe from %appdata% and click OK
– Right click on this policy and select Edit
– Navigate to Computer Configuration –> Policies –> Windows Settings –> Security Settings –> Software Restriction Policies
– Right click on Software Restriction Policies and click on ‘New Software Restriction Policies’
– Right click on Additional Rules and click on ‘New Path rule’ and then enter the following
information and then click OK
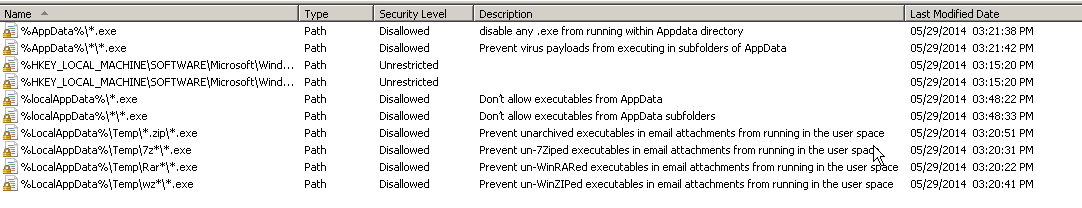
Path: %localAppData%\*.exe
Security Level: Disallowed
Description: Don’t allow executables from AppData (Win 7)
Path: %localAppData%\*\*.exe
Security Level: Disallowed
Description: Don’t allow executables from AppData subfolders (Win 7)
Path: %localAppData%\Temp\*.zip\*.exe
Security Level: Disallowed
Description: Prevent unarchived executables in email attachments from running in the user space (Win 7)
Path: %localAppData%\Temp\7z*\*.exe
Security Level: Disallowed
Description: Prevent 7zipped executables in email attachments from running in the user space (Win 7)
Path: %localAppData%\Temp\Rar*\*.exe
Security Level: Disallowed
Description: Prevent Rar executables in email attachments from running in the user space (Win 7)
Path: %localAppData%\Temp\wz*\*.exe
Security Level: Disallowed
Description: Prevent Winzip executables in email attachments from running in the user space (Win 7)
The following paths are for Windows XP machines (if you still have them; I put these in just in case with the same disallow security settings)
%AppData%\*.exe
%AppData%*\*\*.exe

*Update Feb 02, 2016*
I spent some time on a conference call with some Malwarebytes reps, I’ve been test driving a beta version that’s now available to the public.
Introducing Malwarebytes Anti-Ransomware
As I understand, the good folks at MalwareBytes will be conglomerating all their products: Anti-Malware, Anti-Ransomware, Anti-Malware, and Anti-Exploit into one nice big runtime. (date not yet announced).
11 thoughts on “Disable .exe’s from running inside any user %appdata% directory – GPO”
thepede
I see that this is good for blocking programs from running from those locations and we seem to be specifically pointing out Executables.
My question is: what about .msi files and other types of installers? Would I have to do the same thing for each path but with a *.msi?
thepede
Now that I’m thinking about it, that usually unpacks files and puts it in a temporary folder (often %appdata%) which I guess would normally do so with a .exe? Your thoughts would be appreciated.
arqs
great tutorial to avoid cryptolocker scam
thank you!
Dexter
@thepede. You’re absolutely right, you would need *.msi’s for those exact same paths. Keep in mind some software installer packages can be extracted (.exe) with something like 7zip to the desktop and run the setup.exe.
sipirili
Great info! Just what I was looking for. Unfortunately, upon testing I can still run .exe’s. I made sure that the policy is being applied and still no dice. Any suggestions?
Thanks!
Bill
Be careful here, as you’re still allowing exe’s three sub folders under appdata.
%localAppData%\a\a\cryptowall.exe
Check out this guide for whitelisting apps.
http://mechbgon.com/srp/
Also, the NSA’s guide is useful.
https://www.nsa.gov/ia/_files/os/win2k/application_whitelisting_using_srp.pdf
John
Two questions:
1) Would a generic “\Temp\*\*.exe” cover those Zip/7-Zip/Rar/WinZip lines? If not, wouldn’t the 7-Zip, Rar and WinZip need to be *.ext\*.exe, e.g., %localAppData%\Temp\*.Rar\*.exe
2)%AppData% seems to be used by other versions of Windows, as well. Shouldn’t similiar rules for sub-folders and archive formats be employed?
John
One other comment, to address the .msi question (and maybe the permutations of sub-folders), The Designated File Types has many file types, including .exe and .msi. Could we just simply have policies for these two paths:
%localAppData%
%AppData%
EM
Great article – thanks
Timothy Takemoto timtak
Thank you very much indeed. I added all those restrictions and the same paths with .msi
I have Win7 Home so first of all I used this
https://www.youtube.com/watch?v=tKKU-Mgqz1w
to install GPEdit. I tested the download with malwarebytes and kaspersky first.
I think that these are essentially registry entries (I read that GPEdit is a registry editing tool) so it would be cool if some kind person could make a registry editing file to add all the above restrictions.
I would be interested in answers to John’s questions and a response to Bill’s worry.
And alas, like siprili I find that I can still run exe in the appdata folder. I found a do nothing exe
http://superuser.com/questions/381103/is-there-a-windows-exe-that-does-nothing
and then copied it into Appdata and it ran afaik without any error message.
Maybe I have stopped some system process that executes group policies? This is the first time I have attempted to use them.
Comments are closed.