Guacamole is new to me. I’ve heard of it via reddit forums, but never really paid much attention to it. It just so happened that I was reviewing some Synology Docker / Container videos and stumbled upon using Guac, with a reverse proxy, on a synology, and that’s when I became really interested in the project. Guacamole, for anyone unfamiliar is sort of a gateway to other remote systems behind your home firewall. The basic premise is that it can create connections to all your home/remote devices at the edge network without having to do direct or custom port redirections for each device. One device to connect to all remote / internal.
Which means on the ‘dirty side’ of the firewall I connect via https and 2FA, and a trusted IP address. Once connected to my Guac console, I can move around my home network as if I was sitting in my home office.
This requires a bit of tinkering, and my solution, while not finalized is pretty close to being completed. Big shout out to Digital Aloha for making the video, and is where the majority of my steps originated from.
Here’s my setup:
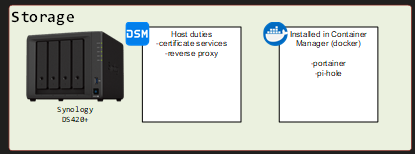
The synology will carry out the certificate and reverse proxy duties. I’m aware there’s docker containers like ngnix that can accomplish this, but I built this with what I had readily available. Synology also offers certificate re-keying services via let’s encrypt, which I have to say, I didn’t really know about until recently.
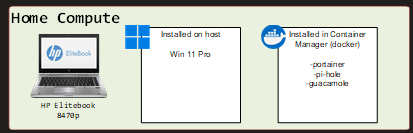
I run a HP elitebook with a docker container for my experiments. As it is right now, this works pretty good, and has the same basic setup as the NAS with a docker install + some images. The Guacamole image resides here
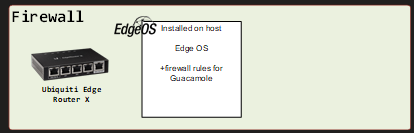
You’ll also need to poke a hole in whatever firewall you’re running as well, for my lab I was using a Edge Router X series with Edge OS.
Let’s start with the Docker Guacamole image configuration on the HP.
Docker / Portainer configuration
I use Portainer because it’s easier to move around the docker sub-system, plus the web-interface I like and it gives up-to-date information without having to click all around. For this example, when I mention ‘host’ that’s whatever is hosting the docker instance.
From your portainer Url, goto -> Stacks -> Add stack
Name: guacamole
Build method: web editor
version: '3.6'
services:
guacamole:
image: unsafetypin/guacamole
environment:
- EXTENSIONS=auth-totp
volumes:
- ./config:/config
ports:
- "8585:8080"
restart: always
8585:8080
*This image also pulls 2FA via auth-totp, more about that in the next step.
Once pasted, deploy the stack, usually takes about 5 – 10 minutes to pull the image and configure to your host network.![]()
Once deployed, it shows in Stacks or containers: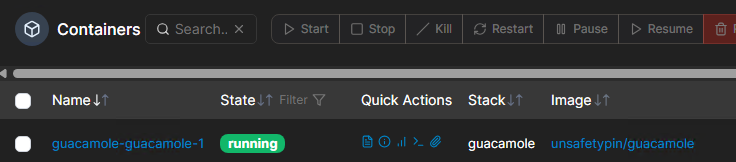
Configure Guacamole accounts
Visit http://host-IP:8585, you should be greeted with the default login screen.

The default username/password is guacadmin/guacadmin
On first configuration, with auth-totp register 2FA with the account.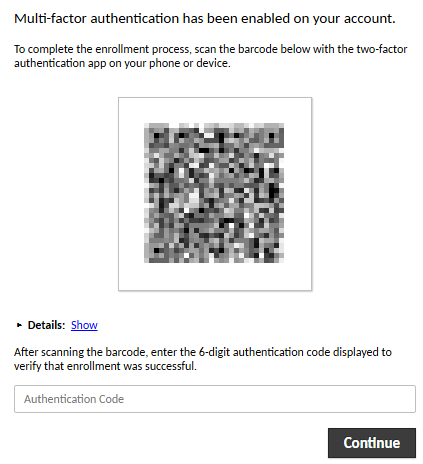
To change password goto Settings -> preferences -> change password
I also suggest creating at least one other account as a “back-door”. Whatever new account you create is enforced with 2FA.
Let’s create an RDP connection to a windows computer within our local network.
Guacamole RDP Connection
From Guacamole goto Connections -> +New connection
- Name: Connection name, hostname, computer function
- Protocol: RDP
- Parameters -> Network-> Hostname: Suggest the hostname, or IP address (provided you use a static value)
- Port: 3389
- Authentication -> Username: I don’t suggest filling out any username/password information since Guacamole asks for this information before connection
- Security Mode: <leave blank>
- Ignore server certificate: [check yes]
- Display -> Resize method: “Display Update” virtual channel (RDP 8.1+)
- Save
You can choose additional settings, these worked for me as a default RDP connection. Points 7 and 8 both need to be updated to the shown values in order to function properly.
Guacamole SSH Connection
From Guacamole goto Connections -> +New connection
- Name: Connection name, hostname, computer function
- Protocol: SSH
- Parameters -> Network -> Hostname: I’m a little stingy about SSH, especially over web. Strongly suggest the IP.
- Port: 22
You can choose additional settings, these worked for me as a default SSH connection.
Now let’s configure the Synology with DDNS, Certificate and the Reverse Proxy itself
DSM DDNS setup
In your Synology DSM, goto control panel -> External Access -> DDNS
- Add DDNS
- Service Provider: ‘Synology’
- Hostname: whichever hostname you’d prefer for external access (ie.Tommysynology)
- Test connection
- Copy the DDNS hostname for the next step below (ie. Tommysynology.synology.me)
*you may already have something here if you’re using Quickconnect
DSM Certificate setup
In your Synology DSM, goto control panel -> security -> Certificate
- Add a new certificate
- “Get a Certificate from let’s Encrypt”
- For domain name, use the “DDNS hostname” from the previous step 5 above
- Enter email for the cert
- For the SAN (Subject Alternative Name) use *.DDNS hostname, (ie. tommysynology.synology.me) to use wildcard certificates
DSM Login portal / Reverse Proxy setup
In your Synology DSM, goto control panel -> Login Portal -> Advanced ->Reverse Proxy -> Create
- Reverse Proxy Name: ‘guacamole’
- Source
- Protocol: HTTPS
- Hostname: Reverse Proxy name + DDNS value (ie. guacamole.tommysynology.synology.me)
- Port: 443
- Enable HSTS [check yes]
- Destination
- Protocol: HTTP
- Hostname: host-IP where the Guacamole docker container lives
- Port: 8585
- Save
Firewall config for Guacamole
From your firewall, configure a port-forward rule that states:
Any tcp-443 traffic from the outside, forward to the synology (where your reverse proxy resides), on port 443. Look up your router documentation for any help. A ubiquiti port forward looks like this:
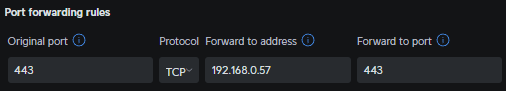
Test from an external source, and you’re golden!
Some anecdotal experimentation information:
I was having trouble deploying this to the synology docker / container image because it actually requires a PUID / PGID, part of the DSM linux operating system. Marius hosting has a pretty good tutorial that uses the DSM container manager, as well as deploying to Synology with portainer. Marius hosting uses this in portainer:
services:
guacamole:
container_name: Guacamole
image: jwetzell/guacamole
healthcheck:
test: curl -f http://localhost:8080/ || exit 1
mem_limit: 6g
cpu_shares: 1024
security_opt:
- no-new-privileges:false
restart: on-failure:5
ports:
- 8348:8080
volumes:
- /volume1/docker/guacamole:/config:rw
environment:
PUID: 1026
PGID: 100
TZ: Canada/Edmonton
EXTENSIONS: auth-totp
The port (8348) can thankfully be changed in this example. Look at my ‘guacamole on synology’ for the full guide.

