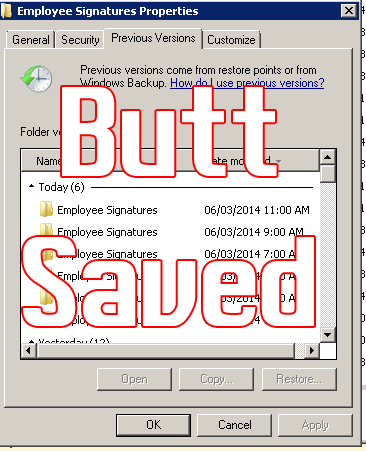
Volume Shadow copy has saved my butt on file, exchange, and SQL servers. Typically, IT departments discourage previous versions on desktops mainly because it opens up issues with disk space and if it’s really worth saving or rescuing an MP3
Read More
Tag: Windows 2008
GPO add corporate picture to your AD logon account
Group Policy to set default Windows 7 Account pictures.
Configuring NPS on Server 2012 with Cisco WLC: Part 2
In part 1 of this tutorial, I stepped through configuration of the Cisco Equipment and configuration of the Network Policy Server with Certificate. In this tutorial, I’ll show you how to tie it all up in Group Policy. This tutorial
Read More